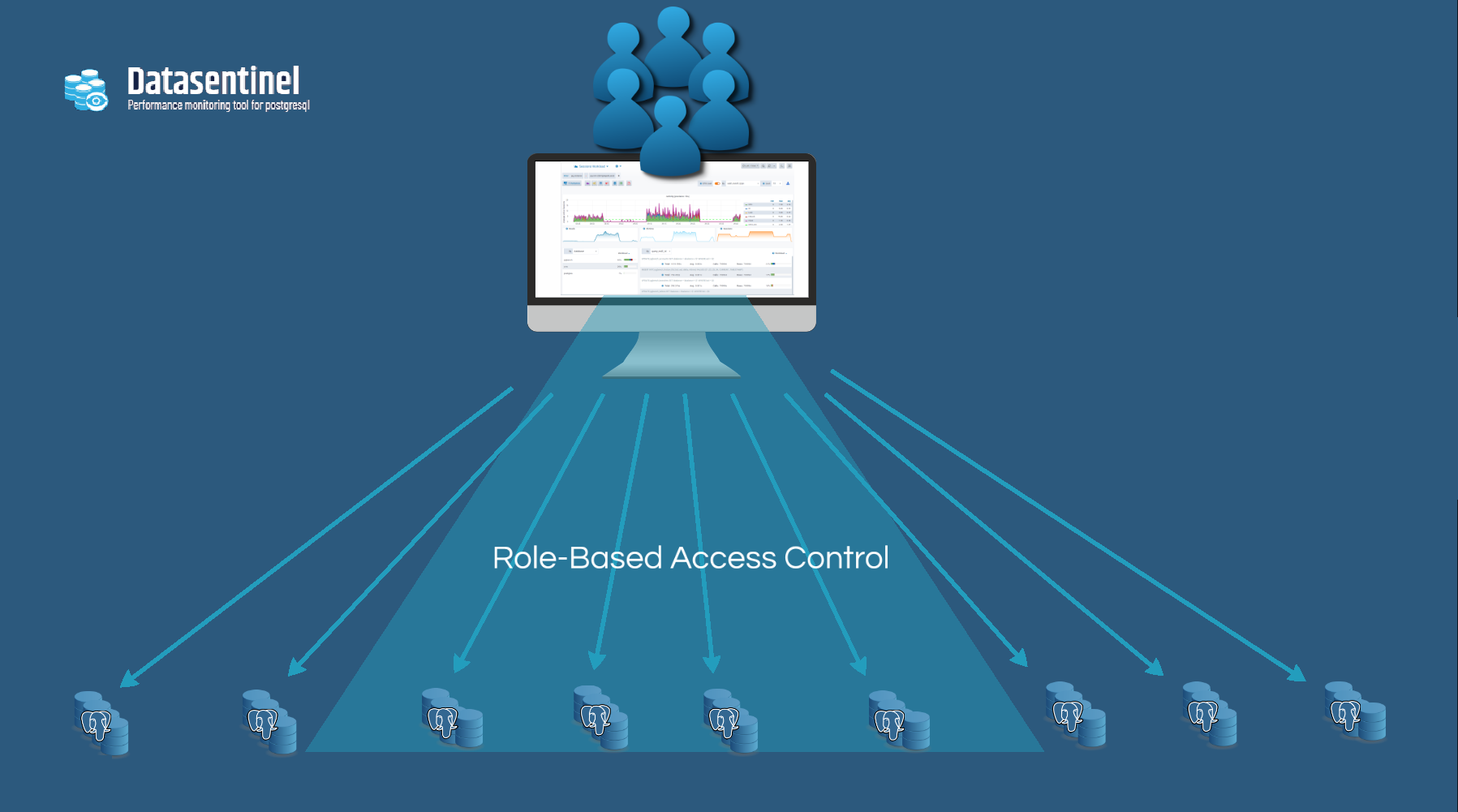
Find out how to secure, manage and automate access to Datasentinel platform
Datasentinel employs a multi-layered approach to secure user access to its platform and control who can access monitored PostgreSQL instances.
Firstly, authentication is enforced through a secure login process that requires users to provide valid credentials before accessing the platform.
Additionally, the platform supports integration with LDAP and Active Directory, allowing for centralized user management and authentication.
In this article, we delve into the ways in which Datasentinel enables organizations to customize user access based on their unique needs through the use of its Role-Based Access (RBAC) feature.
With the association of tags with each monitored instance (Refer to How to use TAGs efficiently), administrators can easily identify and manage user access according to specific criteria such as access to activity statistics of clusters attached to an application or access to non-production instances (the selection criteria for user access is limitless).
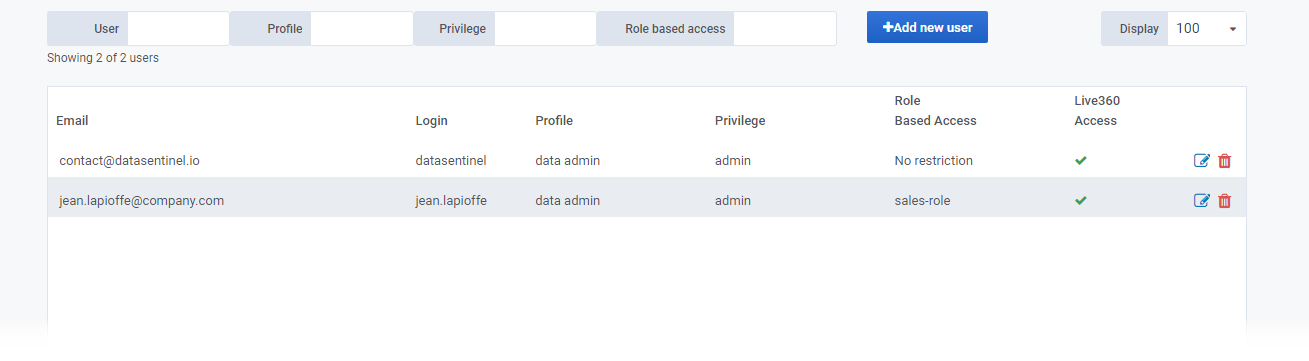
The users
Datasentinel has a default account called “datasentinel” that is granted administrator access when the platform is installed.
This account can be used by administrators to configure roles and users, simplifying the platform administration process.
1. There are two user profiles available in Datasentinel, which enables administrators to restrict access to specific dashboards
| Profile | Description |
|---|---|
| developer | Limited access to Top queries, Session History, Top tables / indexes dashboards as well as the corresponding reporting in PDF format |
| data admin | Access to all dashboards as well as reporting in PDF format |
Default profile: data admin
2. There are 3 privileges:
| Privilege | Description |
|---|---|
| read | Read only access to the platform |
| read write | read privilege + possibility of kill sessions / backends from the GUI |
| admin | read write privilege + platform administration |
Default privilege: admin
3. Accessibility to the Live360 feature (Direct access to instances) can also be configured. (Enabled by default).
User dashboard:
The roles
Roles in Datasentinel are created by associating tags with a collection of values, which can be customized by the administrator.
The roles enable the administrator to restrict user access to specific PostgreSQL clusters in Datasentinel by associating them with users.
Role management can be performed both through the platform’s interface and its available API
You can associate multiple tags to the same role and combine AND/OR conditions. See Documentation
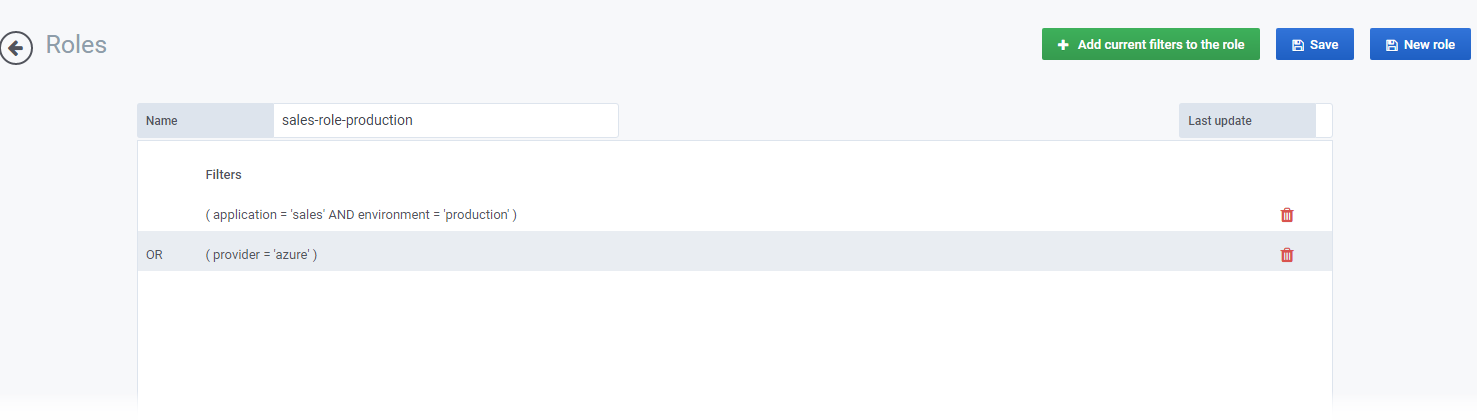
When creating one or more roles in Datasentinel through the graphical user interface or API, the tags must already be associated with the monitored instances
API management example
To create a user with access only to PostgreSQL instances associated with the sales application in Datasentinel, an administrator account must first generate an access token.
An example is provided as follows.
curl -sk -u datasentinel:$PASSWORD -X POST https://$DATASENTINEL_HOST/ds-api/user-token
# Answer
{
"user-token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE2MjY3OTg1MjIsImlhdCI6MTYyNjcxMjExNywiZGF0YWJhc2UiOiJkcy1kYXRhIiwiZW1haWwiOiJjb250YWN0QGRhdGFzZW50aW5lbC5pbyIsInVzZXIiOiJkYXRhc2VudGluZWwifQ.YhKtqrx0O3_gw63dIFCW30ScI8yS-_QY1dss3rRNZNI"
}The access token is valid for 24 hours.
Declaration of a Postgres instance to monitor.
The sales value is associated with the application tag in the tags property.
TMP_JSON_FILE=/tmp/connection.json
CONNECTION_NAME=pg-sales-production
cat > $TMP_JSON_FILE <<EOF
{
"host": "51.158.70.115",
"port": 9342,
"user": "datasentinel",
"password": "sentinel",
"tags": "application=sales"
}
EOF
curl -sk --header "user-token: $ACCESS_TOKEN" --header 'Content-Type: application/json' -X POST https://$DATASENTINEL_HOST/ds-api/pool/pg-instances/$CONNECTION_NAME -d @$TMP_JSON_FILE
# Answer
{
"status": "Connection created and connected!"
}The example above involves managing the instance in Agentless mode .
When using local agents, the instance declaration is performed at the agent level.
More information on this can be found in the Documentation.
Creating a role
The role “sales-role” is created with a tag named “application” and a value of “sales” as its filters.
For more complex role management, such as associating multiple tags with a role, the administrator can refer to the Documentation
TMP_JSON_FILE=/tmp/role.json
ROLE_NAME="sales-role"
cat > $TMP_JSON_FILE <<EOF
{
"access": [
{
"filters": [
{
"tag": "application",
"value": "sales"
}
]
}
]
}
EOF
curl -sk --header "user-token: $ACCESS_TOKEN" --header 'Content-Type: application/json' -X POST https://$DATASENTINEL_HOST/ds-api/roles/$ROLE_NAME -d @$TMP_JSON_FILE
# Answer
{
"status": "Role sales-role created successfully"
}Creating a user with access restriction
A user is created using its email address, and the role previously created is associated with the user to restrict the access to instances with the tag “application” equal to “sales”.
For complete management, refer to the Documentation
TMP_JSON_FILE=/tmp/user.json
ROLE_NAME="sales-role"
USER_EMAIL="jean.lapioffe@company.com"
cat > $TMP_JSON_FILE <<EOF
{
"password": "myPassword",
"role": "$ROLE_NAME"
}
EOF
curl -sk --header "user-token: $ACCESS_TOKEN" --header 'Content-Type: application/json' -X POST https://$DATASENTINEL_HOST/ds-api/users/$USER_EMAIL -d @$TMP_JSON_FILE
# Answer
{
"status": "User with login jean.lapioffe created successfully"
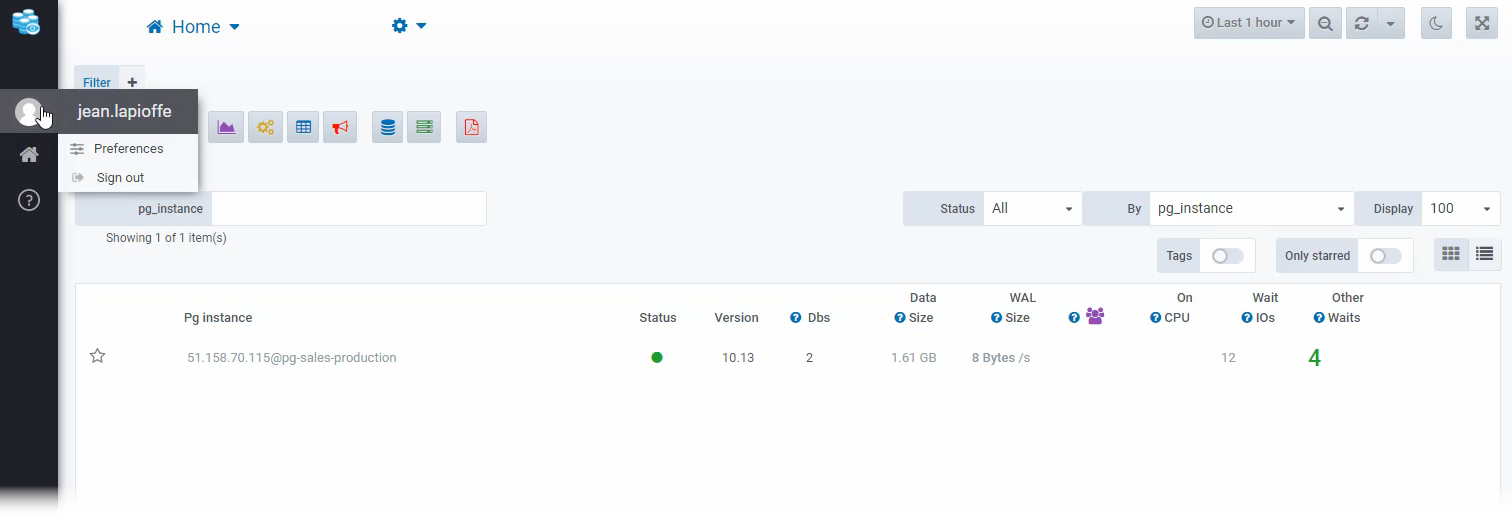
}The newly created user can access the platform using its email address. The user’s access is restricted to instances with the tag “application” equal to “sales”. **
Datasentinel home page:
For comprehensive API usage details, refer to our Documentation section.
For practical examples of API utilization, consult the Datasentinel Toolkit.
Conclusion
Datasentinel provides a platform for managing user access with restrictions, which can be done through an API for automation.
Its user-friendly GUI and unique features make it easy for users to quickly and precisely analyze the workload of all their PostgreSQL instances, whether high availability or not.
Stay connected!